|
SCOUG OS/2 For You - July 1994The Secure Workplace - For Desktop SecurityHave you ever wanted to take your computer to a Team OS/2 demo but were afraid that your carefully crafted desktop would be destroyed? Do you get tired of loading programs on a store machine that you know will be inoperable the next day? Ever fumble for the location of an item using someone elses system? Enter "The Secure Workplace." The Secure Workplace is a desktop security program from Syntegration. While other programs perform similar functions, none that I have seen match the price/performance and Workplace Shell integration achieved here. Whether you want to secure your deskto during a demo, prevent your children from getting into desktop trouble, stop a beginner from trashing their own setup, make a store machine tamper proof or setup a large secure LAN, The Secure Workplace has something for you. Installation is easy, although the installation program is not as polished as the rest of the user interface. After you tell the program where to find OS/2, the installation informs you as it adds functions. Once complete, your system is ready for action. Special Templates Provide Security You start with the addition of several templates to your templates folder that give you Secure Programs, Secure Folders, Restricted Folders and Password Folders. You use these new secure templates the same way that you would any other templates with the addition of separate pages for setting local and global passwords and the details of how secure you want your setup to be. By checking boxes, you decide whether you want to be able to copy, move, shadow, delete, rename, drag, select, sort, arrange or get the details view of an object. This makes it extremely easy to protect your desktop with a minimum of fuss using a very intuitive user interface. The Secure Program template allows creation of a program object that you can use without restriction, but most menu options are removed and optionally the settings are password protected. This function could be used to lock an icon in place and prevent accidental deletion, sorting, etc. without removing the ease of using that program object. Great for new users, or for tech support. Since you can lock an item in place, remote tech support personnel can direct a user to the exact location of an object without fear that the object has been moved or destroyed. This also prevents "adventurous" new users from making an irrecoverable error before they learn the ropes. The Restricted Folder works the same way as the Secure Program but with a folder instead of an individual program. Again, this can be used to protect a folder that contains programs shared among users. A note of caution is needed here, however. Creating a Restricted Folder and dropping program objects into it does not make the objects secure. You must use the Secure Program template to do that. 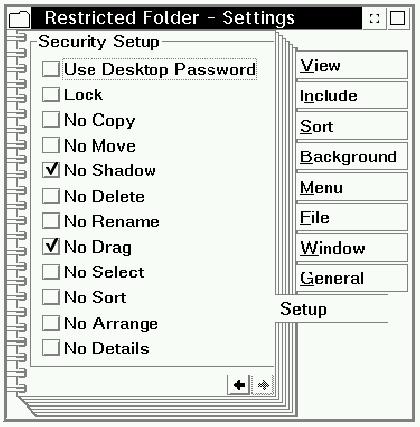
The Password Folder goes one step further in protecting your programs. As the name suggests, it password locks the folder so that unauthorized personnel cannot open it. In addition, it optionally has a different password for unlocking the settings of th folder. It shares the features of the Secure Folder. The Password Folder could be used to limit entry to critical program objects to knowledgeable people while keeping newer users away from the heart of OS/2. The Secure Folder is not really meant for an end user. Everything from opening the folder to adjusting any setting to opening a program is password controlled. This would generally be used for very sensitive data or those few very vital objects that the user would not need to deal with. Now on to the other utilities provided with The Secure Workplace. The Window List Manager is another tool to prevent the end user from making an end run around your security protection. With it, you can make a window list entry invisible, or grayed out, along with making the program "non-jumpable." This means that when you cycle through the open programs using <alt> - <esc>, a non-jumpable program will be skipped. This is very useful in a LAN environment when you want the server window to be transparent to the user. You can use this utility from the command line, or interactively through a PM object. The Object-Maker is a script file that allows you to make custom objects. While an end user may find this tedious, a LAN manager would be able to use this to update or restore all of the systems under his control with one script, saving a great deal of time per system. The Secure Workplace comes with sample files to get you started. The Object Relocator uses a REXX script to move existing program objects to new locations, again allowing for easy and uniform customization of a series of desktops. What's in the near future for desktop security? Well, how about a Log-On Folder that would allow for remote log-on to a LAN and then create that user's particular custom folder on the machine they are using at the time. The folder is destroyed upon log-off, allowing a user to go anywhere and still have their familiar setup waiting for them. Can't you see the opportunities here? In Conclusion The Secure Workplace allows the end user to decide how much security is needed on a particular system. It allows tech support to rely on programs and documentation being where they should be. It provides the new user with a reliable, consistent desktop. For a suggested retail price of $59.95, The Secure Workplace is cheap insurance for your system. The Secure Workplace is available in both a single user version ($59.95) and a broader enterprise edition ($549 for a 10 workstation license). For more information about this product, contact Syntegration, 13241 Norton Avenue, Chino, CA 91710; phone(909) 464-9450; FAX (909) 464-9438. It can be found at Indelible Blue, Inc., (800) 776-8284; The Corner Store, (800) I-BUY-OS2; and locally at Office Solutions, (800) 897-APPS or (310) 439-5567.
P.O. Box 26904 Santa Ana, CA 92799-6904, USA Copyright 1994 the Southern California OS/2 User Group. ALL RIGHTS RESERVED. SCOUG is a trademark of the Southern California OS/2 User Group.
|








